Countering ARP spoofing with iptables
Mardi 19 décembre 2023, par Jérémy DE COCK
Many use a DHCP server to manage the assignment of IP addresses within their network(s) (ISC-DHCP, Dnsmasq, Microsoft DHCP Server, etc.). But very few protect themselves from ARP spoofing, which is a very famous old attack, but which is still as formidable as ever. Protecting against it requires resources in terms of equipment, e.g. a switch with anti arp spoofing mechanisms or supporting 802.1X, or technical expertise, e.g. fixing the ARP table on the machine hosting the DHCP service.
Maybe not so new, but still a threat, so here is our solution...
Solution
In the DHCP service configuration, we have all our @MAC / @IP pairs and we know that Netfilter provides a module for managing MAC addresses with IPTables rules. Based on this, we've developed a script that will retrieve this information and generate our firewall rules. Of course, we've added a few extra features...
Prerequisites
The script requires several things: firstly, it is a BASH script, so it must be run on a Linux environment that has BASH (which shouldn't be a problem these days).
The script will directly set up the iptables rules on the machine and also save them in the /etc/iptables.rules file. Nftables is therefore not managed and the value of the output file must be modified directly in the code.
As mentioned above, a Kernel module is required for the script to function properly, but in reality 3 are needed:
- CONFIG_NETFILTER_XT_MATCH_MAC : to compare MAC addresses in rules
- CONFIG_NETFILTER_XT_MARK : to define markers on rules
- CONFIG_NETFILTER_XT_MATCH_MARK : to compare markers on rules
To check that these modules are activated or can be activated, simply use the following command:
$ cat /boot/config-`uname -r` | grep [MODULE] | grep "y\|m"
In our case, we use ISC-DHCP, the script gets the @MAC / @IP pairs stored in the file /etc/dhcp/dhcpd.conf:
host test {
hardware ethernet a1:b2:c3:d4:c5:6e;
fixed-address 192.168.1.15;
}
How it works?
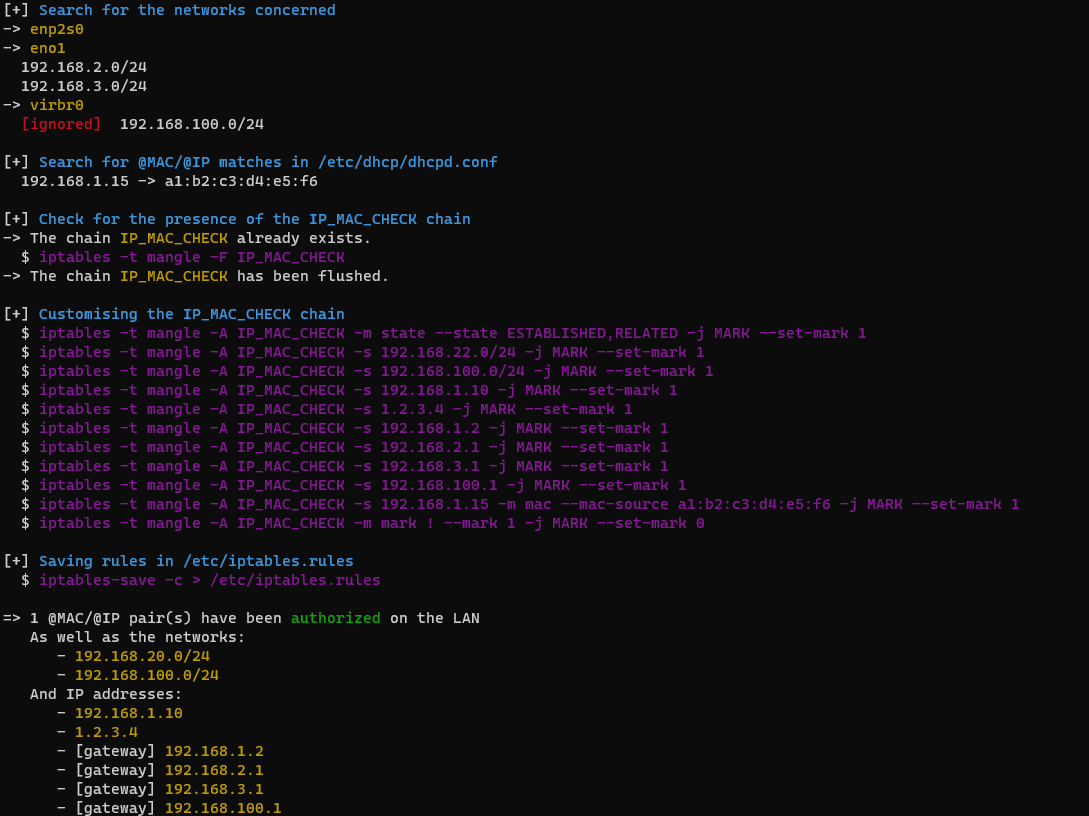
- If we run the script on our test machine, it will automatically retrieve the IP addresses assigned to the various interfaces mounted on the machine: physical + bridges.
- It will then retrieve the @MAC / @IP pairs stored in /etc/dhcp/dhcpd.conf.
- The IP_MAC_CHECK string will be created in the MANGLE table.
- All rules relating to interfaces found on the machine, IP addresses / networks whitelisted by the user are set in the IP_MAC_CHECK chain, they set a marker to 1 if they are triggered. The last rule set up corresponds to a default rule which sets a marker to 0 if and only if no marker has been set up to that point.
- A rule is placed in the FORWARD chain of the MANGLE table to redirect all traffic to IP_MAC_CHECK (FORWARD since we only want to filter traffic from our secondary interfaces).
- A final rule is placed in the FORWARD chain of the FILTER table to reject all packets with a marker set to 0.
- The rules are saved in the /etc/iptables.rules file.
If you want to see an example of how to use the tool, we encourage you to check it out on our Github.